Top 10 Vulnerabilities of Wireless Communication Instructure
A062021-Vulnerable and Outdated Components was previously titled Using Components with Known Vulnerabilities and is 2 in the Top 10 community survey but also had enough data to make the Top 10 via data analysis. Introduction to Network Security maintains its focus on the network and its vulnerabilities protocols and security solutions.

Wireless And Mobile Device Security 9781284211726
A rogue access point is a wireless access point that is illicitly placed within or on the edges of a Wi-Fi network.

. Top 10 Cyber Vulnerabilities for Control Systems 5 Vulnerability 4. 74 AES and ECB. In such complex heterogeneous systems communication links must meet stringent requirements on throughput latency and range while adhering to tight energy budget and providing high levels of security.
In order to establish two way communications a wireless link may be using radio waves or Infrared light. The 7 most common wireless network threats are. As of December 2019 Chinese state cyber actors were frequently.
Wireless domain and to propose innovations that could potentially address these shortcomings. All three of these vulnerabilities are related to Microsofts OLE technology. This category moves up from 9 in 2017 and is a known issue that we struggle to test and assess risk.
Bandwidth Stealing Outside intruders can connect to wireless access points. There are a number of vulnerabilities in the security protocols listed above. Within the enterprise rogue access points are commonly referred to as insider threats and they have typically been encountered among employees who wish to have Wi-Fi access within organizations that do not have Wi-Fi.
Vulnerabilities of wireless networks devices and protocols. Insertion attacks Insertion attacks are based on deploying unauthorized devices or creating new wireless. Inspired by the SANS Top 20 this list is a consensus of industry experts on wireless and mobile vulnerabilities that require immediate remediation.
Federal Express has been using a type of wireless networks common to the 80211 networks used today but the general public has recently just started to use wireless networking technology. Inadequately secured wireless communication including microwave technologies Before installing wireless its important to do a complete assessment to identify the best areas for wireless use and ensure that leakage out of the plant is minimized. Use of unsecured wireless communication for control system networks.
It is the only category not. Of the top 10 the three vulnerabilities used most frequently across state-sponsored cyber actors from China Iran North Korea and Russia are CVE-2017-11882 CVE-2017-0199 and CVE-2012-0158. It includes network architecture the functions of layers in a typical network and network based attacks including header protocol.
It is offered as a public service by the Mobile. Up to 20 cash back Other noteworthy vulnerabilities in our top detections include the SambaCry Linux vulnerability the OpenSSL Heartbleed bug the remote code execution CVE-2014-9583 router vulnerability and the remote code execution CVE-2017-6361 Network Attached Storage NAS vulnerability. We implement both preventative and detective mechanisms as well as processes controls and tools in layershelping to mitigate risks that.
Provides this list of the Top 10 wireless network risks. Excerpts regarding 3 of the 10 listed vulnerabilities are given below. Wireless communication devices include cellular phones cordless phones and satellite phones smart phones like Personal Digital Assistants PDA two way pagers and lots of their devices are on their way to improve this wireless world.
Use of inappropriate wireless communication. Wireless sensors and actuators connected by the Internet-of-Things IoT are central to the design of advanced cyber-physical systems CPSs. Because of weak security that exists in wireless networks companies such as Best Buy have decided to postpone the roll-out of wireless technology.
Our security program is built based on ISO 27001 NISTs Cyber Security Framework AICPAs Trust Services Principles and Criteria and SANS CIS Critical Security ControlsAnd we develop our applications abiding with OWASPs Top 10. Believe it or. Built-in wireless LAN encryption such as.
We describe some of these vulnerabilities in the following sections. This covers insecure data storage and unintended data leakage. This new category is a combination of M2 and M4 from Mobile Top Ten 2014.
Sending large amounts of traffic or viruses over the network with the intent of hijacking resources or introducing backdoors. From the input received the Forums Advanced Technology Committee selected the following as the revised Top 10 Innovations that have the most potential of improving the wireless communications experience. Wireless intrusion detection systems WIDS are also needed to protect control systems which use wireless communications.
71 Wireless Networking and Security with Python. Widely publicised weaknesses and inherent vulnerabilities of prevailing 80211 wireless networks have necessitated network defence strategies that proactively secure such systems. Criminal Activity - An unauthorized user.
Wireless data requires data encryption. 72 Ceasar Cipher and Frequence Analysis. This covers poor handshaking incorrect SSL versions weak negotiation clear text communication of sensitive assets etc.
Rogue Access Points. Wireless LANs are a natural extension to RSA SecurID token deployments. Wireless Vulnerabilities Threats And Countermeasures Information Technology Essay.
Lack of authentication in the 80211 series of wireless communication protocols. 73 Vigenere Cipher and One-Time Pad. Conventional IDS systems like Snort or TippingPoint are capable of detecting common attacks against TCPIP based systems and some attacks against control systems in Ethernet layers 3 and 4 and in some cases layer 7 54.
Here are the top 10 ways your network can be attacked from inside and what you can do to insure your business never has to perform an exorcism on your servers. By using the Internet connection to download music games and other software they reduce employee productivity.

Vulnerability Management In Ics Patching Configuration Devices Quarantine Study Com
Hnap Protocol Vulnerabilities Pushing The Easy Button Blog Tenable

8 Step Network Vulnerability Assessment Process Vulnerability Cyber Security Program Cyber Security Career

Vulnerabilities In Industrial Control Systems Ics Study Com

Owasp Top 10 Most Critical Security Risks 2013 Security Cyber Security 10 Things
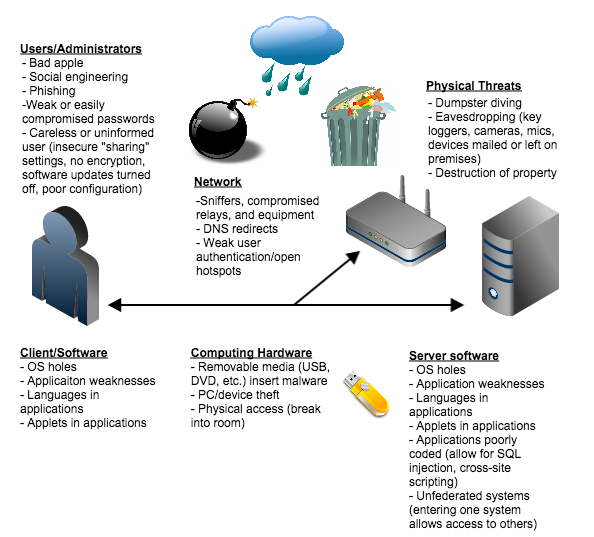
13 3 Where Are Vulnerabilities Understanding The Weaknesses Information Systems

Project 1 Vulnerability Memo Hmgt 300 Introduction To The U S Studocu

Top 10 Penetration Testing Companies And Service Providers Rankings
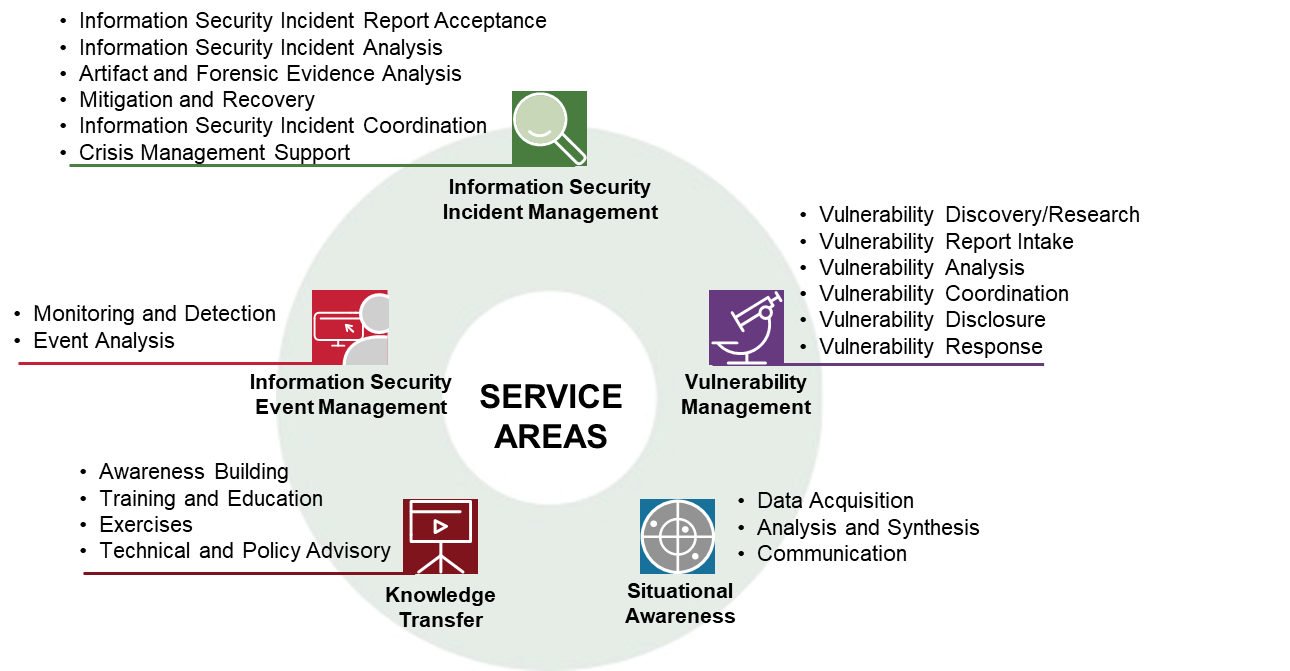
Csirt Services Framework Version 2 1

Bluetooth Vulnerabilities Bluejacking Bluesnarfing Study Com

Certification Roadmap Grey With Color 20x30 Printready 848a Us 03 Roadmap Technology Roadmap Cyber Security Certifications
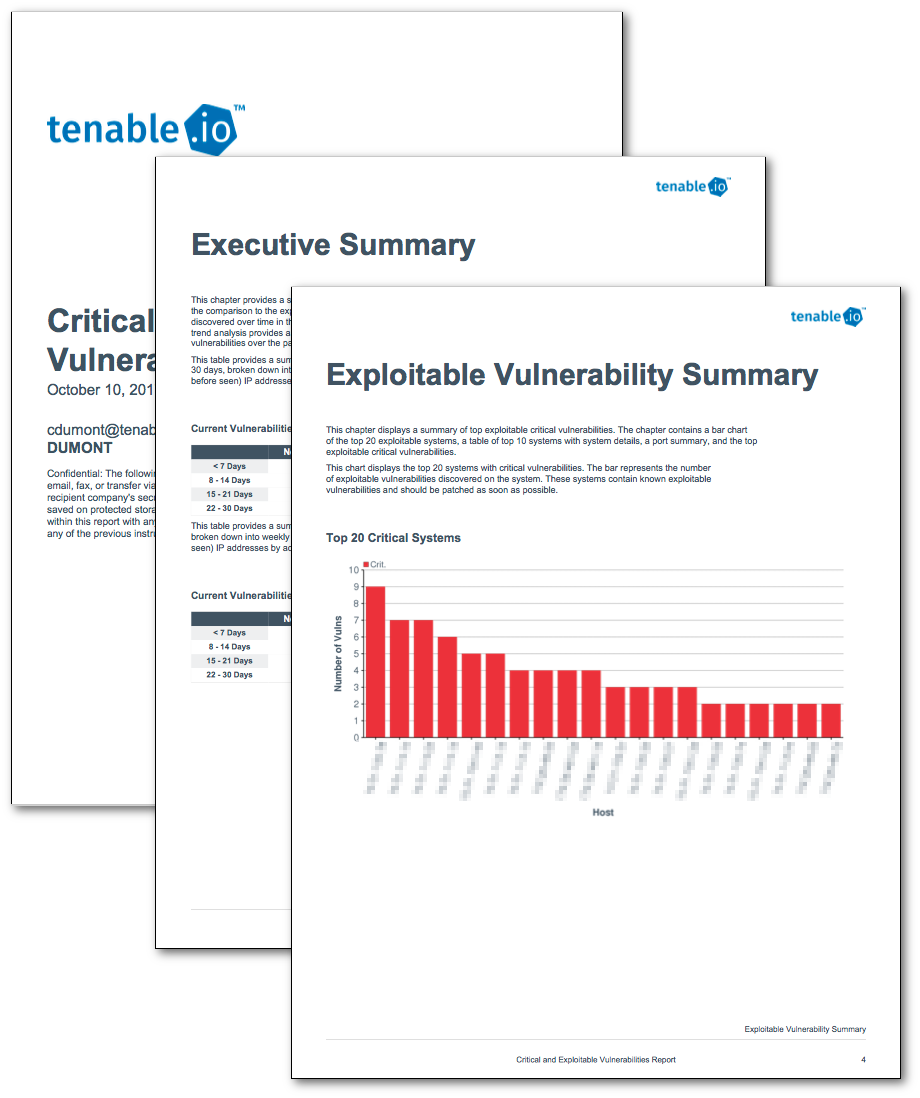
Critical And Exploitable Vulnerabilities Report Tenable Io Report Tenable
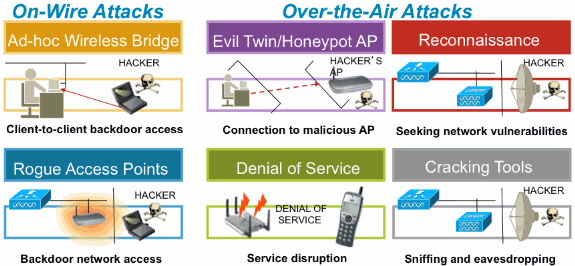
Adaptive Wips Elm Configuration And Deployment Guide Cisco

Bluefruit Le Sniffer Bluetooth Low Energy Ble 4 0 Nrf51822 Bluetooth Low Energy Low Energy Computer Security

Comptia A Training Types Of Networks Types Of Network Comptia A Computer Learning

Wireless And Mobile Device Security 9781284059274

Discover How Ai Can Improve Cybersecurity Cyber Security Cyber Security Technology Artificial Intelligence

Fighting Covid 19 And Future Pandemics With The Internet Of Things Security And Privacy Perspectives

0 Response to "Top 10 Vulnerabilities of Wireless Communication Instructure"
Post a Comment